Protect Your Web Servers: New HTTP/2 DoS Attack Can Crash Web Servers With a Single Connection
In the ever-evolving landscape of cybersecurity threats, a newly discovered zero-day vulnerability has emerged, posing significant risks to web servers worldwide. Named “CONTINUATION Flood,” this flaw exploits weaknesses in the HTTP/2 protocol, potentially leading to denial of service (DoS) attacks and server crashes with just a single TCP connection. As businesses increasingly rely on online platforms for their operations, understanding and mitigating these vulnerabilities are paramount to safeguarding digital assets and maintaining uninterrupted service.
What is Zero-Day Vulnerability?
A zero-day vulnerability refers to a security flaw in a software application or system that is exploited by attackers before the developer becomes aware of it. The term “zero-day” implies that the developers have had zero days to fix or patch the vulnerability, leaving users at risk of exploitation.
Zero-day vulnerabilities are particularly dangerous because they are unknown to the software vendor and, therefore, no patches or fixes are available. This gives cybercriminals the advantage of being able to launch attacks without detection or defense.
Zero-day attacks in the past
- Stuxnet Worm (2010): Stuxnet is one of the most infamous zero-day attacks in history. It targeted supervisory control and data acquisition (SCADA) systems, particularly those used in Iran’s nuclear program. Stuxnet exploited multiple zero-day vulnerabilities to infiltrate and sabotage the centrifuges used in uranium enrichment.
- WannaCry Ransomware (2017): WannaCry exploited a vulnerability in Microsoft’s Windows operating system known as EternalBlue. This ransomware spread rapidly across the globe, infecting hundreds of thousands of computers in over 150 countries. It encrypted files on the infected systems and demanded ransom payments in Bitcoin for their release.
- Heartbleed Bug (2014): Heartbleed was a critical security vulnerability in the OpenSSL cryptographic library, which is widely used to secure web communications. It allowed attackers to steal sensitive information, including passwords and encryption keys, from servers without leaving any traces.
These are just a few examples of zero-day attacks that have had significant impacts on organizations and individuals worldwide. It underscores the importance of proactive security measures and rapid response to mitigate the risks posed by such vulnerabilities.
Understanding HTTP/2 and its Vulnerabilities
HTTP/2, introduced in 2015, aimed to enhance web performance through features such as binary framing, multiplexing, and header compression. However, recent research by Barket Nowotarski has uncovered vulnerabilities related to the handling of CONTINUATION frames within the HTTP/2 protocol. These frames, designed to stitch together header and trailer sections of HTTP/2 messages, lack proper limitations and checks in many implementations.
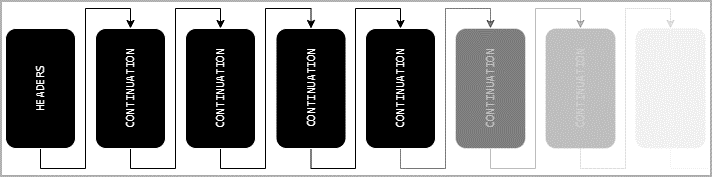
Exploitation and Impact
Exploiting these vulnerabilities, threat actors can send an endless stream of CONTINUATION frames without setting the ‘END_HEADERS’ flag, leading to out-of-memory crashes or CPU resource exhaustion on affected servers. The severity of these attacks is underscored by their ability to disrupt services with just a single HTTP/2 TCP connection. Various implementations, including Node.js, Envoy, Tempesta FW, amphp/http, and Apache Httpd, have been identified as vulnerable to different degrees of DoS attacks.
Vendor Response and Mitigation
CERT Coordination Center (CERT-CC) has issued alerts listing CVE IDs corresponding to affected HTTP/2 implementations. Vendors and libraries such as Red Hat, SUSE Linux, Apache HTTP Server Project, and Node.js have acknowledged the impact and are working on patches and updates. However, mitigating these vulnerabilities requires proactive measures, including patching vulnerable systems and libraries, implementing header size limits, and enabling advanced frame analytics to detect malicious requests.
“Given that Cloudflare Radar estimates HTTP traffic data above 70% of all internet transfer and significance of affected projects I believe that we can assume that large part of internet was affected by an easy-to-exploit vulnerability: in many cases just a single TCP connection was enough to crash the server” warned Nowotarski.
An alert from the CERT Coordination Center (CERT-CC) published this week lists several CVE IDs corresponding to different HTTP/2 implementations vulnerable to these attacks.
These implementations allow varying levels of denial of service attacks, including memory leaks, memory consumption, and CPU exhaustion, as described below:
- CVE-2024-27983: Affects Node.js HTTP/2 server. Sending a few HTTP/2 frames can cause a memory leak due to a race condition, leading to a potential DoS.
- CVE-2024-27919: Affects Envoy’s oghttp codec. Unlimited memory consumption due to not resetting a request when header map limits are exceeded.
- CVE-2024-2758: Relates to Tempesta FW. Its rate limits are not effectively preventing empty CONTINUATION frames attacks, potentially allowing DoS.
- CVE-2024-2653: Affects amphp/http. It collects CONTINUATION frames in an unbounded buffer, risking an OOM crash if the header size limit is exceeded.
- CVE-2023-45288: Affects Go’s net/http and net/http2 packages. Allows an attacker to send an arbitrarily large set of headers, causing excessive CPU consumption.
- CVE-2024-28182: Involves an implementation using nghttp2 library, which continues to receive CONTINUATION frames, leading to a DoS without proper stream reset callback.
- CVE-2024-27316: Affects Apache Httpd. Continuous stream of CONTINUATION frames without the END_HEADERS flag set can be sent, improperly terminating requests.
- CVE-2024-31309: Affects Apache Traffic Server. HTTP/2 CONTINUATION DoS attack can cause excessive resource consumption on the server.
- CVE-2024-30255: Affects Envoy versions 1.29.2 or earlier. Vulnerable to CPU exhaustion due to a flood of CONTINUATION frames, consuming significant server resources.
Challenges for Server Administrators
Addressing these vulnerabilities poses challenges for server administrators, as malicious requests may not be readily visible in access logs without advanced frame analytics enabled. The complexity of debugging and mitigating these attacks underscores the importance of equipping administrators with adequate HTTP/2 knowledge and resources.
Rapid Cyber Team’s Recommendations for CSOs:
The discovery of CONTINUATION Flood vulnerabilities in HTTP/2 underscores the evolving nature of cyber threats and the critical need for proactive security measures. As threat actors continue to exploit emerging vulnerabilities for malicious purposes, businesses must remain vigilant and prioritize the protection of their web servers.
By understanding these vulnerabilities, collaborating with vendors for timely updates, and implementing robust security measures, organizations can mitigate the risk of DoS attacks and safeguard their online presence.
- Understand your external and partner network’s connectivity to remediate any Internet-facing systems with the mitigations below.
- Understand your existing security protection and capabilities you have to protect, detect, and respond to an attack and immediately remediate any issues you have in your network.
- Ensure your DDoS Protection resides outside of your data center because if the traffic gets to your data center, it will be difficult to mitigate the DDoS attack.
- Ensure you have DDoS protection for Applications (Layer 7) and ensure you have Web Application Firewalls. Additionally, as a best practice, ensure you have complete DDoS protection for DNS, Network Traffic (Layer 3), and API Firewalls.
- Ensure web server and operating system patches are deployed across all Internet Facing Web Servers. Also, ensure all automation like Terraform builds and images are fully patched so older versions of web servers are not deployed into production over the secure images by accident.
- As a last resort, consider turning off HTTP/2 and HTTP/3 (likely also vulnerable) to mitigate the threat. This is a last resort only because there will be significant performance issues if you downgrade to HTTP/1.1.
- Consider a secondary, cloud-based DDoS L7 provider at the perimeter for resilience.
Rapid Telecom‘s mission is to fortify your networks and enhance your cybersecurity posture. We are dedicated to providing comprehensive solutions that safeguard your digital assets and ensure uninterrupted operations. With a commitment to innovation and excellence, Rapid Telecom is here to support you in navigating the evolving landscape of cybersecurity threats.


